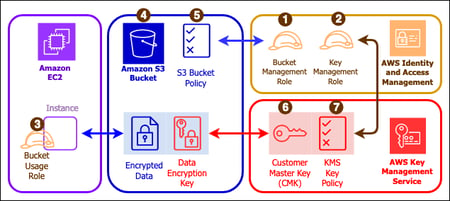
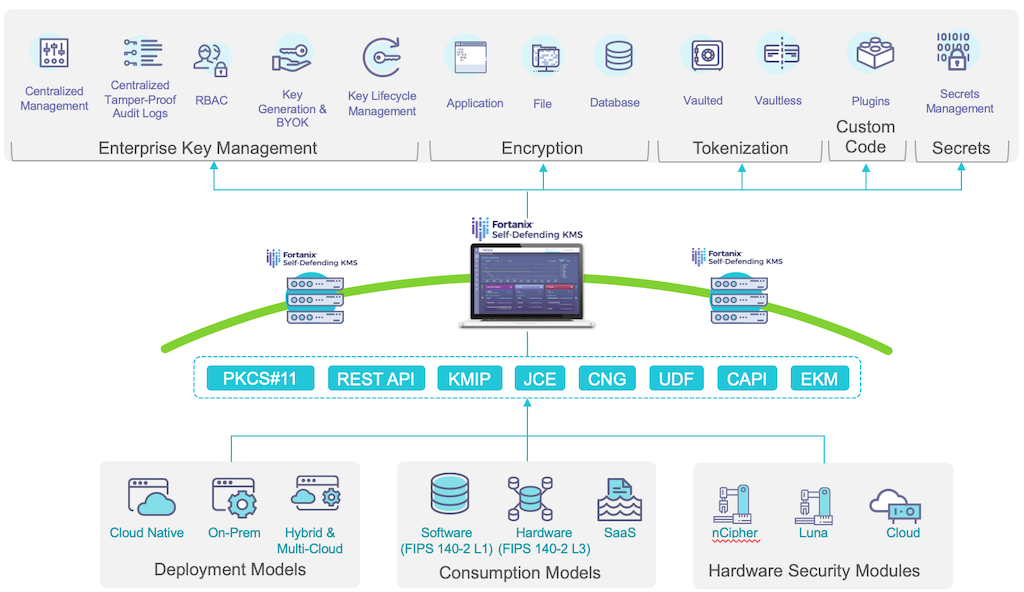
Demystifying KMS keys operations, bring your own key (BYOK), custom key store, and ciphertext portability | AWS Security Blog

Use Key Management Service (AWS KMS) to securely manage Ethereum accounts: Part 1 | AWS Database Blog
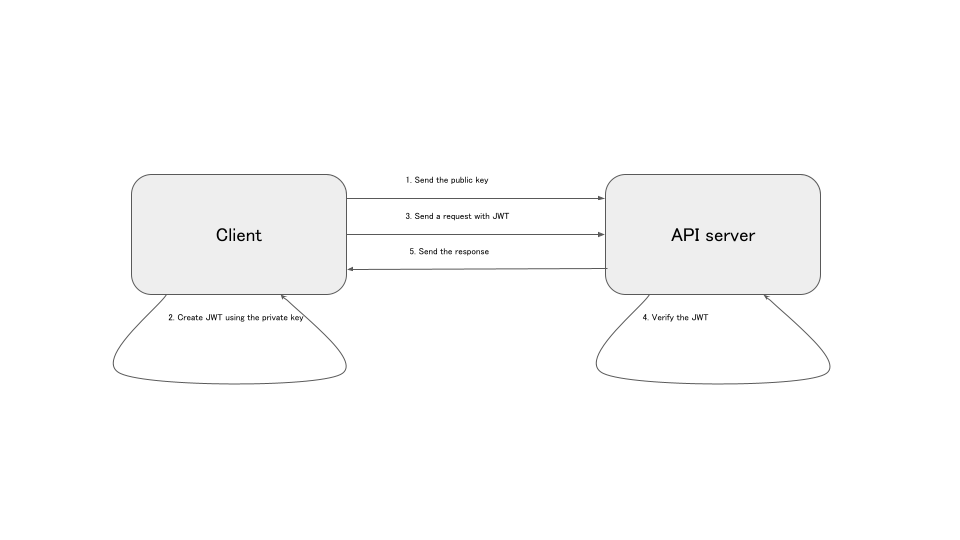
Create JSON Web Tokens with signatures by ECDSA_SHA algorithms signed by AWS KMS keys with python - Money Forward Developers Blog